Zero Trust Network Access: Barracuda's ultimate guide - Free Download
The cybercrime threat landscape is more saturated than ever, with attacks growing in sophistication and successfully hitting organizations in every sector. What’s also growing is the financial damage to these businesses: IBM Security reported a 10% increase in the average total cost of a breach from 2020 to 2021 — the largest increase in a single year in the last 7 years. To avoid the growing financial risks, businesses urgently need to rethink their security postures — traditional security methods are no longer cutting it.
What is Zero Trust Network Access?
While ‘Zero Trust’ sounds somewhat negative, the model is actually one of enablement, not restriction. It allows for better remote access, improved performance, better productivity, and strengthened security.
A good way of understanding Zero Trust is to compare it to moving through an airport. When you arrive at the check-in desk, you need to authenticate your identity with your passport. This gets you through one stage of the process of making your journey across borders.
How to implement Zero Trust Network Access:
1. To successfully implement ZTNA, first you need to map out the surface you will protect. This should include all the critical data that you hold — for example, personally identifiable information, credit card information, and any intellectual property.
2. Next, identify who needs permission to access these data sources, applications, assets, and so on. Implement single sign-on (SSO), a method of authentication that allows your users to securely access multiple sites and applications with a single set of credentials.
3. Enable multifactor authentication (MFA), which requires users to verify their authentication attempts with another device, ensuring that the request was genuine. This makes the source of truth more robust and reduces the likelihood of impersonation
4. Lastly, make sure that there is a strict endpoint device validation process in place. Ensure that all devices for all users are registered and that you have a directory that includes the device ID, serial number, model, and operating system.
How Barracuda can help:
As it becomes more apparent that employees are increasingly in favor of remote or hybrid work situations, the need for ZTNA applies to more businesses than ever before — and some that may never have expected to rely on devices outside of the traditional perimeter. Making sure that every single one of these devices is both secure and verified sounds like a massive task, but it doesn’t have to be.
Zero Trust is a philosophy revolving around the concept that no one should be automatically trusted with access to networks or assets. It involves managing permissions and access so that users are granted specific access to only the data or applications they need.
Featured Product
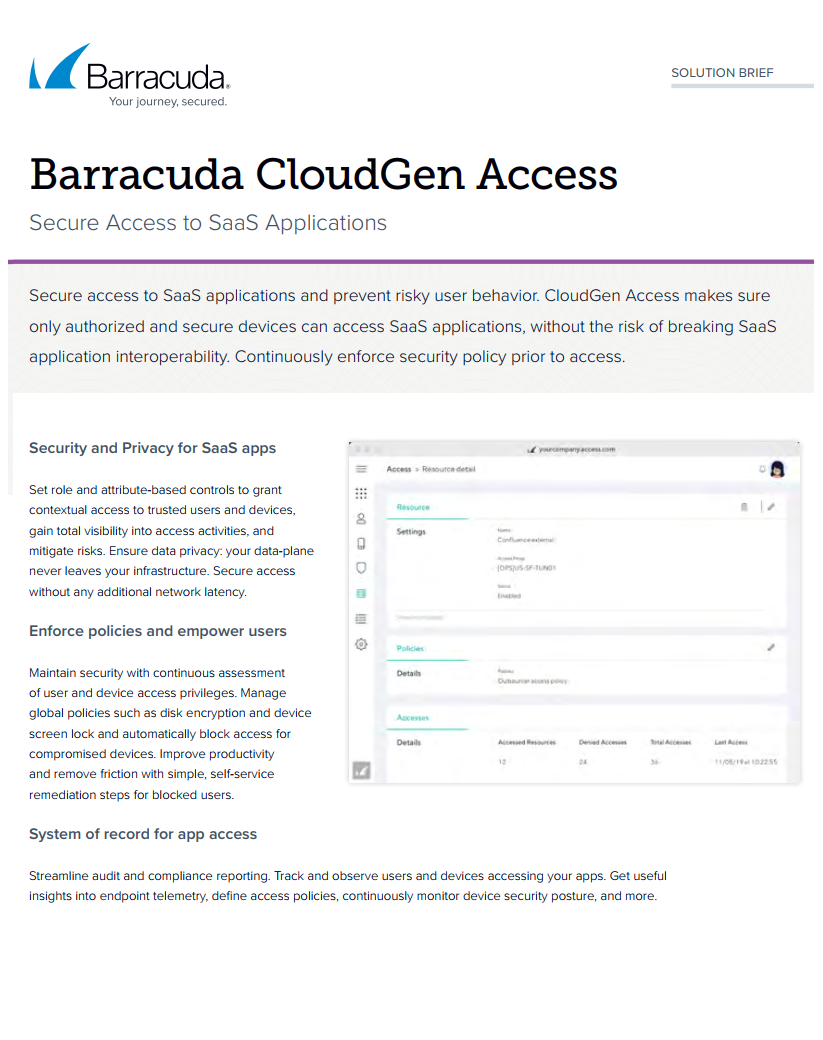
Barracuda CloudGen Access is an innovative Zero Trust Access solution that provides secure access to applications and data from any device and location. CloudGen Access continuously verifies that only the right person, with the right device, and the right permissions can access company data or apps, or any infrastructure.
- Quick to deploy, easy to manage
- Secure contractor access to your business
- Accelerate DevOps and Kubernetes deployments
Our sales team is with you every step of the way through the buying process, it's that simple.
With over 20 years of experience, our expert team is genuinely interested in your needs and can help you today.